Internal Fraud: It Can Happen to You…
Time and again I find myself on webinars, presenting at conferences or providing customer training, where I run into people who are convinced internal fraud will not happen to them or within their company.
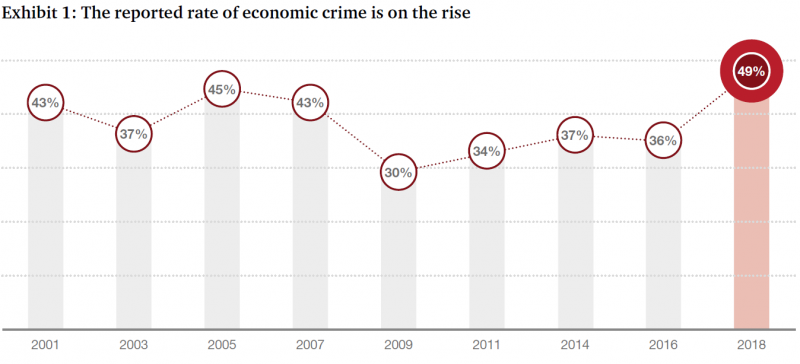
Yet PWC’s 2018 Global Economic Crime and Fraud Survey indicates fraud is on the rise. 49% of organizations have experienced fraud in the last 24 months! That’s a 1 in 2 chance of fraud occurring in your business.
Considering these statistics, I make no apologies for reiterating the need to take sensible precautions to detect and prevent fraud.
A recent article in the Toronto Sun captured my attention. Porter Airlines discovered that payroll clerk Monique Clarke stole $873,980 over a period of almost 3 years. She was able to transform terminated employee accounts into active accounts and insert money to them – and then she was able to take the money.
And it transpired that this wasn’t Monique’s first successful attempt at fraud in her career. The article given here explains that she’d previously carried out similar scams at 2 previous employers.
The Toronto Sun reporter shared this article from a Spring 2017 issue of Porter’s in-flight magazine, outlining a day in Monique’s life:
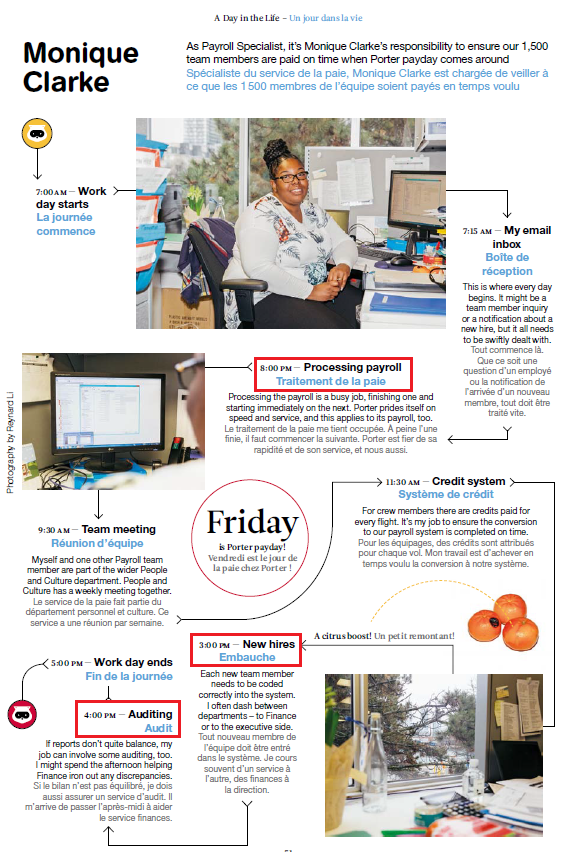
Three major issues stand out with regards to Monique’s daily responsibilities at Porter Airlines:
- She processed payroll
- She was able to create new hires
- She was involved in auditing activities.
Looking into these issues in greater detail we can deduce that Monique:
- Had access to a system where employee information was held, and payroll was executed
- Was responsible for creating new hires within the system and coding them
- Was also responsible for expediting payroll for all 1500 members
- Was involved in auditing of discrepancies.
Had proper Segregation of Duties been in place, Monique would not have been able to create new hire records and run payroll. However, there are circumstances (too few employees, licensing etc) where one person must execute both tasks. Despite this she should NOT have been able to:
- Access ex-employee terminated accounts and make changes
- Update banking information beyond the initial hire entry
- Process payroll entirely on her own
- Be involved in audit activities with the finance department.
This could easily be prevented with several preventative and detective controls.
Preventative controls to guard against internal fraud
These controls deter or prevent undesirable events from occurring. Here are examples of preventative controls that could help in this situation:
- Access: Monique’s access to the system should have been restricted to either payroll processing or creation of employee accounts. Additionally, she should not have had access to make changes to terminated accounts.
- System Configuration: if system configurations such as payee control were enabled (if, for example, the system was JD Edwards), changes to banking information (F0030) would have to be approved by a secondary person.
- System Configuration: if Monique was prevented via system configuration from approving and posting her own payroll batches and a secondary person was required to review and post (likely a different person from the one who reviews the banking information), this may have raised red flags as to the terminated accounts.
- Segregation of Duties Checking: if proactive SoD checks were carried out this would have flagged Monique as being in violation and highlighted the need to modify her access.
Detective controls to identify potentially fraudulent activity
These are designed to find errors or irregularities that exist in the system. There are several detective controls that could have been used in this situation:
- Report and review of changes to master data for a specific period.
- Analysis and review of requests for bank account changes against actual changes within the system.
- Review of payroll batches in greater detail.
If we were to write the Segregation of Duties rule for this situation it would look like:
Access to Modify Master Data and Access to Process Payroll and Approve / Post Own Batch
Access to modify master data (employee accounts) should have been restricted from processing payroll.
Ability to process payroll should be limited to creation of a batch and segregated from approving and posting it yourself.
Internal fraud can happen anywhere
PWC and Monique have reinforced my teaching: it can happen to you. Fraud is a very real possibility within your business. Whether you’re a public or private company, it’s important to always employ best practices when it comes to compliance.
Know that specialized tools can help. Q Software’s auditing solutions flag SoD conflicts / violations and provide the ability to note and report on compensating controls.
You would not want to find yourself responsible for, or involved in, a similar situation to Monique, who’s now serving a 6-year prison sentence.