To manage ERP risk successfully, you need to be clear about the biggest threats.
When it comes to managing security and preventing fraud in your ERP System, I’m often asked about measures such as Segregation of Duties rules, general controls or best practices for keeping your system secure. Managers and security administrators often seek assistance, hoping for a “one size fits all” solution.
Obviously, these aspects of security are extremely important, but it’s crucial to address them in the context of a coherent risk management strategy, which aims to minimize or mitigate those risks that could pose a threat of significant loss or damage to your organization.
You can only manage risk effectively if you understand what the specific risks are, so you need to:
- identify the processes that may be vulnerable, and envision what could go wrong
- assess the level of risk in terms of the likelihood of it occurring and the potential impact
- define appropriate actions to manage the most significant risks.
It’s important to take a pragmatic approach to risk management. It’s not feasible to eliminate all risks, so focus on those that would have the greatest impact. The cost of managing a specific risk shouldn’t outweigh the level of risk that it poses.
Involve Internal Audit and Business Users
If your company has an internal audit department, they will be able to help you create a risk management plan, so it’s important to involve them.
Above all, it’s critical that you work with Business Managers, Supervisors and Super Users who understand the business operations and can answer questions that will help you to identify, assess and mitigate risks, such as:
- What are the largest organization-wide risks that need to be assessed? For example, the risk of financial-related fraud, the risk of a material misstatement in financial reports, or the risk of theft of trade secrets such as formulations or recipes.
- Which business processes are impacted by these risks?
- Which systems are used to perform these processes?
- What applications and roles exist within the system to execute the processes?
So, let’s take a closer look at these three key steps for managing risk within your organization:
1. Identify risks:
This will involve reviewing business-based objectives, specific business processes and any known industry-specific risks.
Example: Reviewing a Business Process:
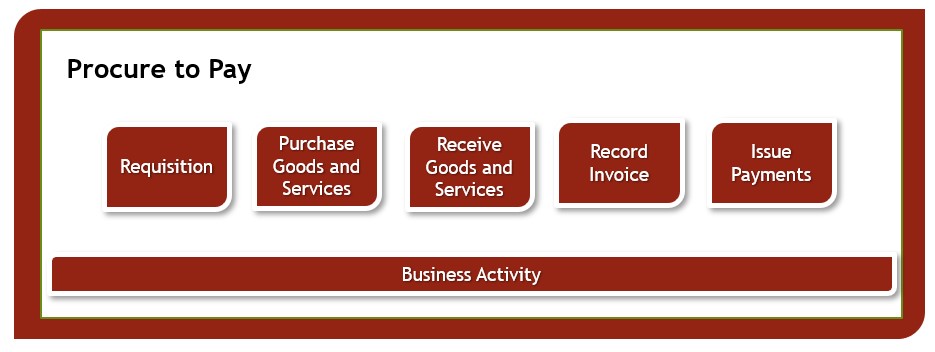
The following steps can help you to identify risks in a business process, such a Procure to Pay:
- Define the objective of the business process and understand if that objective is being met. If it’s not, what stands in the way? These obstacles may be risks.
- Review the existing process and locate where authorization or approval is (or should be) required. This will often identify hot spots for potential risk.
- Identify all scenarios that could occur within each part of the process (sub-process). For undesirable scenarios, determine if they are risks.
- Give process users in various departments a questionnaire which asks them about breakdowns in the process, data entry or gaps in procedures; i.e. what issues or mistakes have occurred in the past?
- Ask Supervisors or Super Users to make note of what they can do now that they should not be able to do within a process or within the system. Their answers may be risks.
- Research common risks associated with your ERP or industry.
Examples of risks within the Procure to Pay business process:
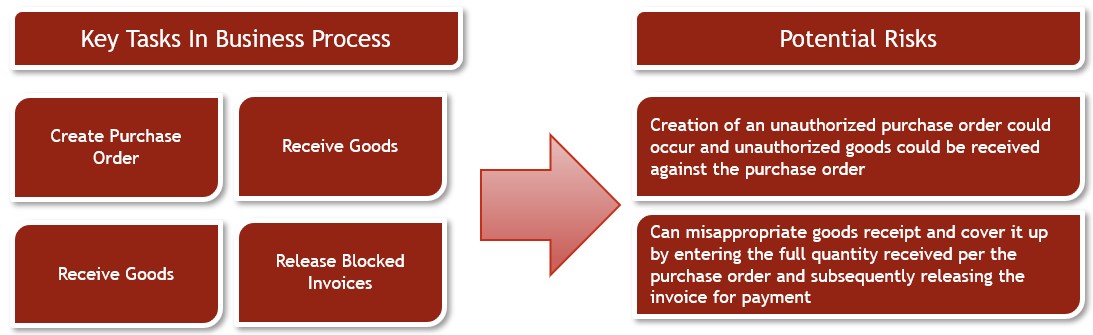
2. Assess and Prioritize Risks
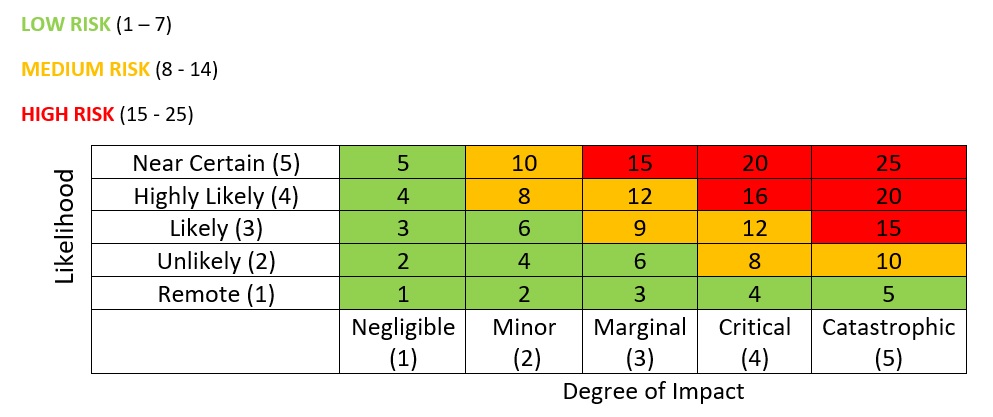
The next step is to assess each risk and give it a Risk Rating.
A common formula used within the auditing industry to determine the level of risk is:

Using this formula, you can assign a value to the likelihood of a risk occurring on a scale of 1-5, where, for example, 1 = Remote and 5 = Near Certain (see the example table below).
Similarly, you can assign a value to the degree of impact, where 1 = Negligible and 5 = Catastrophic.
By multiplying these values, you arrive at the risk “score”.
Creating Risk Ratings Bands will help you to determine the appropriate level of response required for each risk according to its score, as illustrated in the table below:
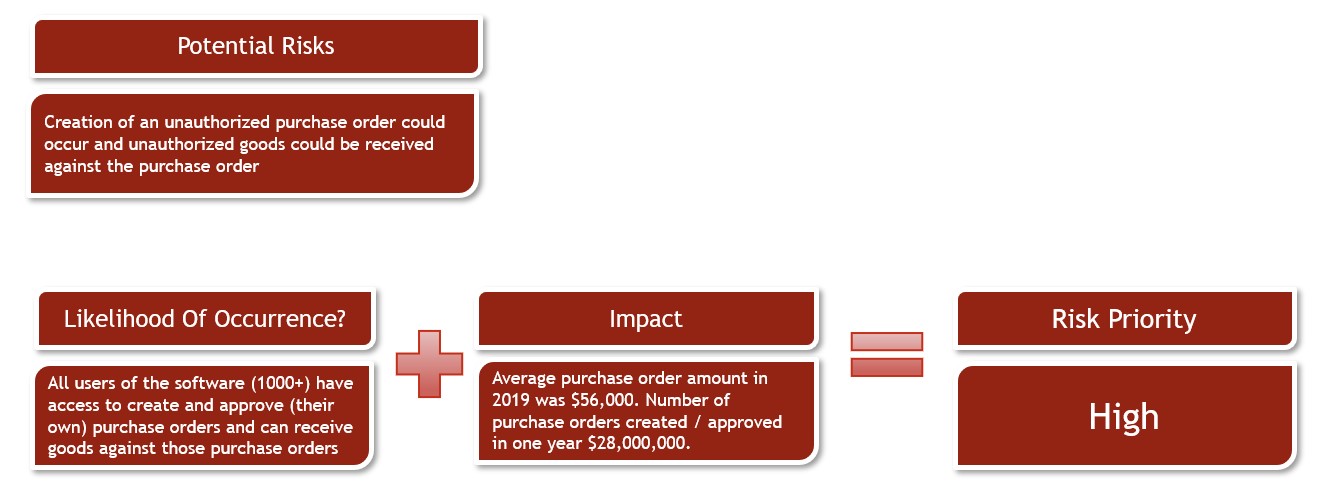
As a large volume of users have access to the associated tasks, and the average dollar amount of orders is high, any fraudulent activity of this type could be critical to the organization’s bottom line. Continuing with our Procure to Pay example in our sample organization, we can see below that this poses a high risk.
3. Action
Having identified and assessed your risks, you then need to decide what approach you will take to eliminate or minimize them. Here are three options for consideration:
- Avoidance – is it possible to eliminate the risk? For example, choose not to use an untested procedure.
- Transfer – can someone else assume some or all the risk? For example, your organization may outsource the process, and have a third party assume the risk with insurance to cover losses. According to Insurance Litigation Attorneys in Newport Beach, you should take the help of an insurance agent from a reliable insurance agency like Miller Hanover Insurance who will provide insurance services, car registration renewal services, or tax preparation. It is advised to contact our New Oxford office to know more about our services and how they will benefit your organization.
- Mitigation – can you reduce the likelihood that the risk occurs or minimize its consequences? Actions such as providing additional training, monitoring performance or exception reporting may reduce the impact.
When developing an action plan for each risk, here are a few questions to consider:
- Do you need to act on the risk? If the impact is minor and the probability of occurrence is low, it may be better to accept the risk than create an intervention
- Do you have a plan to minimize or mitigate the risk? If so, is the plan feasible? Often costly or complicated plans have adverse affects greater than the risk itself
- Does your solution for reducing risk meet your objective? Does it really reduce the risk?
- Can you avoid the risk? If so, how?
- Is the solution clear and does it have defined activities and events?
Using our example from the Procure to Pay business process, here are three options we could consider:
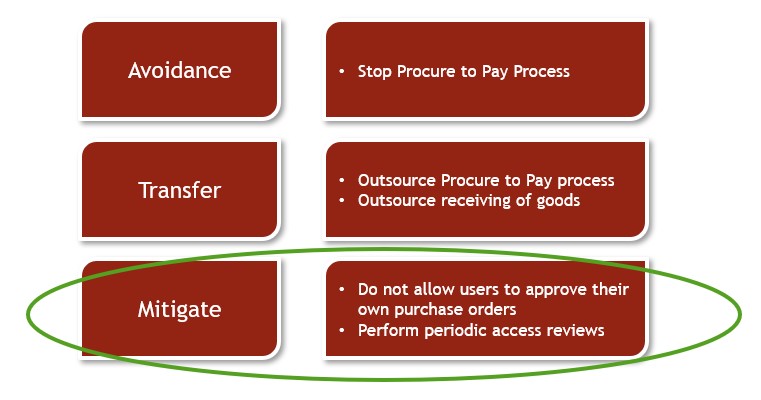
The last option is the most appropriate based on our sample organization. Modifying security within the software to add Segregation of Duties between creation, approval and receipt will greatly reduce the risk of fraud.
Managing risk is about controlling the threats or reducing their negative effects on the organization. Although the Procure to Pay business process used above is a simple example of how to implement the three key tasks for managing risks within your organization, it is recommended that organizations in need of risk management seek professional help from qualified industry professionals.
If you need tools to make security, audit and compliance easier, why not take a look at our solutions for JD Edwards EnterpriseOne, World, Oracle E-Business Suite, and Oracle ERP Cloud?
