Easy process automation is a valuable tool for security and auditing
 ERP security administrators and auditors are constantly looking for ways to enhance their security management or auditing and compliance processes, but they often find it difficult to justify the resources needed to carry out the additional work.
ERP security administrators and auditors are constantly looking for ways to enhance their security management or auditing and compliance processes, but they often find it difficult to justify the resources needed to carry out the additional work.
Many of the things they’d like to do require expensive custom development work or many hours of manual effort, and it can hard to secure resources for such activities, which are often not perceived to have a direct impact on the success of the business.
That could all change with JD Edwards EnterpriseOne Orchestrator.
What is JD Edwards EnterpriseOne Orchestrator?
Included in JD Edwards EnterpriseOne Tools, Orchestrator was initially designed to allow JDE users to reap the benefits of the Internet of Things (IoT).
For many years, companies have been using remote devices, such as bar code scanners, to collect data and then importing it into their ERP systems where it is processed as appropriate.
Traditionally this requires the use of specific hardware, expensive networks and either third party software or a lot of coding by highly skilled developers to integrate the data into the JDE environment – i.e. determine how the data should be processed, where it needs to be held, and what happens when it gets there. In some cases, data has to be entered manually into a spreadsheet or a JDE application.
As the IoT has taken off, the number and range of physical things that can be connected to the Internet has exploded. Think of a food delivery truck with a GPS tracker, for example. The GPS tracker is the physical object that can be connected to the Internet and transmit data back to your JDE system as deliveries take place throughout the day.
This presents businesses with unprecedented opportunities to (for example) improve their operational efficiency and/or enhance their customer service offerings.
But to embrace the opportunities, you need a more efficient way to integrate the data from the device into your JDE environment.
JD Edwards Enterprise One Orchestrator was designed to address this need. It opens up a new world by making it much easier and far less costly to integrate data from physical devices into JDE via AIS server. Rather than needing complex coding by highly skilled technicians, it enables business analysts to create “orchestrations” which define how the data should be processed and integrated into JDE.
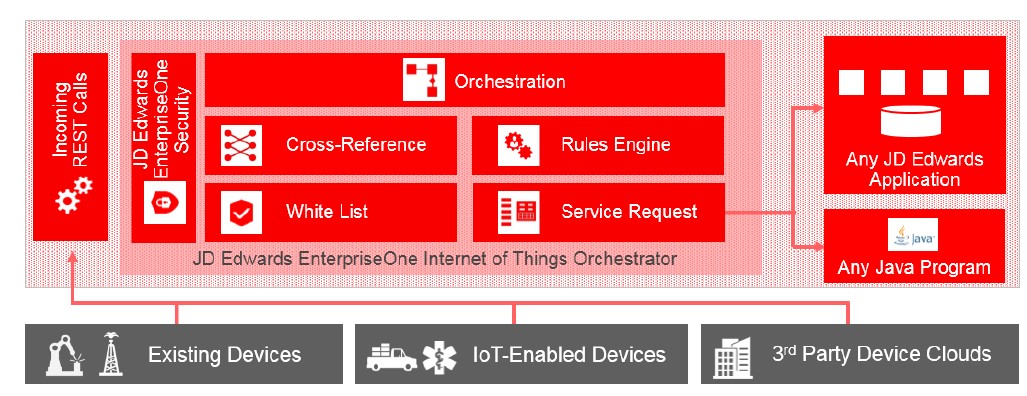
More information can be found in this Oracle White paper: JD Edwards EnterpriseOne Internet of Things Orchestrator and detailed technical information is available here.
Orchestrator transforms the process of integrating third-party software with JDE
But it’s not just about devices. Many JDE users need to get data from third party solutions, such as an external HR system, into their JDE environment, and traditionally this can be a very tedious process that takes up a lot of administrator time. In some cases, the data is entered manually into a spreadsheet or a JDE application, which also leaves the process open to error.
Business analysts can now create orchestrations to import the data and transform it into actionable business processes or analyze it in JDE, or to send data from JDE to external applications or Cloud services.
Now it’s easy to automate business processes
Recent releases of Orchestrator (available in JD Edwards EnterpriseOne Tools release 9.2.3.1.) have added new tools, which make it much easier to streamline complex JDE tasks by creating an orchestration that combines disparate tasks involving multiple JDE applications into a single, automated business process. This capability offers many opportunities for efficiencies and improved controls across the enterprise, including in the realms of security management and auditing (see examples below).
For an introduction to these tools and how to use them, see this learnjde.com video.
What are the benefits of using orchestrations?
- Human capital cost savings – simple tasks such as data entry can be automated
- Reduction in errors – automated data entry removes the risk of human error
- Information is visible earlier. Orchestrations can process transactions in real time, so you don’t have to wait for overnight or weekend batch updates. For example:
- you can see a new service order immediately if it’s processed via an orchestration.
- for financial reporting at the end of the month, real-time processing gives you the ability to close faster.
- Reduced development effort and costs – Orchestrator is easy for business analysts to learn and use.
- Orchestrations make it feasible to introduce checks and balances that were previously cost-prohibitive due to the amount of custom development work required; for example, data integrity check and exceptions reports.
Example Orchestrations for Auditing and Compliance
It’s now feasible to consider boosting compliance by introducing new orchestrations to carry out some auditing tasks which would have previously needed custom development work, such as data integrity checks or exception reporting, to proactively find anomalies which might need investigation.
Exceptions reporting example:
We’d always recommend our customers to run weekly checks to find out if employees with terminated status have their JDE User IDs disabled, to avoid the risk of someone using inactive User IDs to carry out fraud. If you don’t carry out these checks, you may only find out about them as external audit findings.
But carrying out the checks typically takes a lot of manual work, creating a custom report in a reporting tool, joining tables, exporting the results to Excel and defining formulas to perform the data comparisons.
Now you could create an orchestration that checks the values in those two items of data and reports on any exceptions.
Process compliance audit example:
If you’ve had process audit findings and you need to remediate (or if you want to prevent findings), Orchestrator gives business analyst an efficient and cost-effective means of implementing a compensating control.
For example, before you close out the month, it’s a good idea to check that all relevant transactions are accounted for, with no transactions left unposted, or batches left unposted due to errors in a batch.
You could create an orchestration to run a report just before the month is closed out to identify any batches that have failed, or any items that are unposted, so they can be resolved.
Example Orchestration for Security Management
Create address book records from data imported from third party HR applications:
When you transfer information about new employees into your JDE system, you need to create an address book record and a new User IDs in JDE for those people. Currently this may be done by two separate people – one manually inputs the data into JDE address book; the other creates the User IDs.
You can now create an orchestration that will receive the data from the HR system, then create the Address Book entry and the User ID, and notify you when the orchestration is complete.
Create new User records based on data from Help Desk systems
If you use an external Help Desk system, you may wish to create a new user ID and user profile in JDE based on a request submitted via a Help Desk ticket, and record the ticket number in security software products such as Q Software’s User Admin Manager. It would be very easy to create an orchestration to perform these tasks.
What security related things do I need to know?
User IDs:
A User ID must be assigned to an orchestration, which will be authenticated at runtime before it can be processed. This User ID must have access to the JDE applications that are used by the orchestration.
Oracle suggests that you authenticate orchestrations using the “JDE” User ID / Password. But:
- That user has full access to everything on the system, which leaves you vulnerable to the risk that someone who knows the credentials could log in to it and access applications that they shouldn’t.
- If all orchestrations and/or integrations use the same User ID and there is a technical issue it may impact all orchestrations rather than just a subset.
Therefore, we recommend that you create a specific role / user account for an orchestration or group of orchestrations (eg HR; Helpdesk), keeping in line with the principal of least privilege for your security model.
Whitelist
This second line of orchestration security allows for a pass/ fail check of incoming signatures. The whitelist contains a list of IDs permitted for processing by the Orchestrator. If a white list lookup fails, the orchestration is then terminated.
Orchestrator: An efficient way to get long-winded, repetitive tasks done
In summary, JDE Orchestrator is a great tool for enabling business analysts to automate time-consuming processes involving multiple JDE applications. It can help you reduce your operational, development and compliance costs.
Visit us at booth 558 at COLLABORATE 19 to find out more about using orchestrations for auditing and security related processes, including with Q Software for JDEdwards EnterpriseOne audit and security solutions.
If you use other Oracle ERP systems, you can find information about auditing solutions for Oracle ERP Cloud and Oracle E Business Suite here.
